In the realm of cybersecurity and ethical hacking, the Pwnagotchi device has emerged as a fascinating tool for enthusiasts and professionals alike. This palm-sized, customizable gadget has gained popularity for its ability to passively capture and analyze Wi-Fi handshakes, making it an invaluable asset in penetration testing and network security assessments. In this blog post, we’ll explore the Pwnagotchi device, its features, functionalities, and the ethical considerations surrounding its use.
Table of Contents
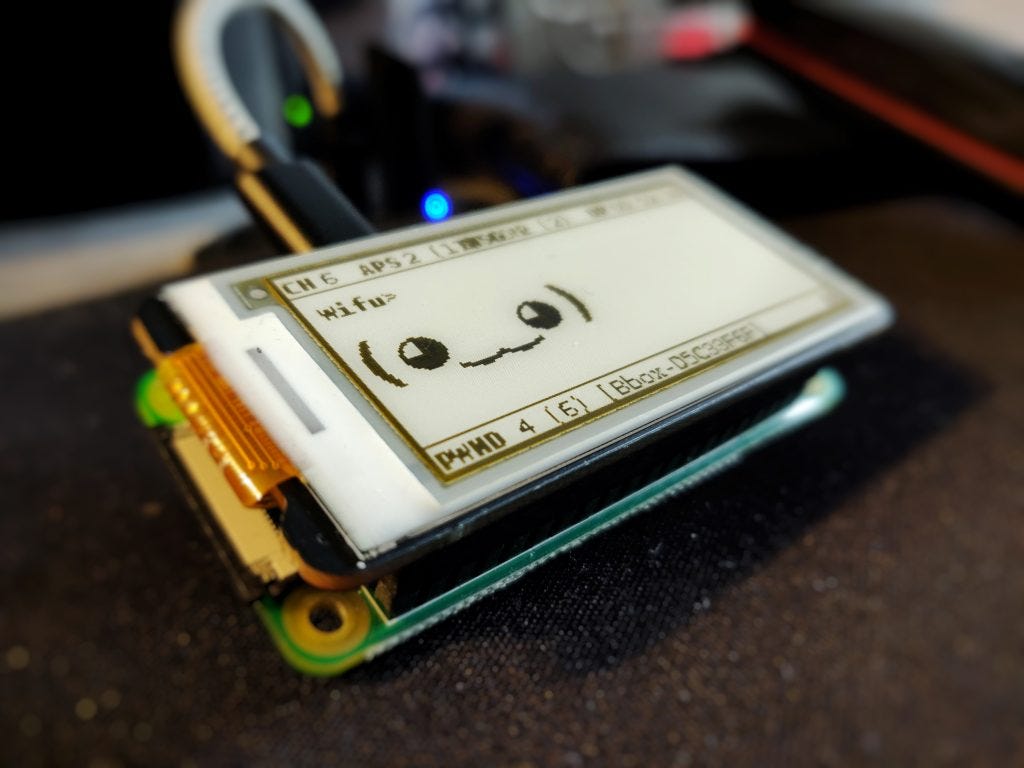
The Birth of Pwnagotchi
The Brainchild of evilsocket
Pwnagotchi was brought to life by Simone Margaritelli, a renowned Italian security researcher and hacker better known by his online alias, evilsocket. Simone has been actively involved in the cybersecurity community, contributing to various open-source projects and sharing his expertise on offensive security techniques.
Inspiration from Tamagotchis
The name “Pwnagotchi” cleverly combines two words: “pwnage,” a term commonly used in the hacking community to signify gaining control or compromising a system, and “tamagotchi,” the iconic virtual pet from the ’90s. Simone drew inspiration from the Tamagotchi, giving his creation a playful twist by integrating a digital pet-like interface into a device with a more serious purpose – WiFi auditing.
A Raspberry Pi-Based Device
Pwnagotchi is built upon the Raspberry Pi single-board computer platform, a popular choice for numerous DIY projects due to its compact size and versatility. This choice of hardware makes Pwnagotchi accessible and customizable for users with varying levels of technical expertise.

Machine Learning and Reinforcement Learning
What sets Pwnagotchi apart from traditional WiFi hacking tools is its innovative use of machine learning, particularly reinforcement learning. This approach allows the device to adapt and optimize its attack strategies based on the outcomes of previous attempts. As Pwnagotchi continuously learns from its environment, it becomes more effective in capturing WiFi handshakes over time.
Open-Source Philosophy
Simone Margaritelli firmly believes in the power of open-source software and community collaboration. Pwnagotchi’s source code, along with its various plugins and extensions, is available on GitHub. This open philosophy has fostered a community of developers and security enthusiasts who actively contribute to the project, expanding its capabilities and ensuring its continuous improvement.
A Playful Exterior for Serious Intentions
The physical appearance of Pwnagotchi is another aspect that adds to its charm. Housed in a 3D-printed case resembling a digital pet, it strikes a balance between playfulness and the serious nature of its intended purpose. This design choice not only reflects Simone’s sense of humor but also serves to make the device inconspicuous, allowing users to carry out Wi-Fi auditing discreetly.

Understanding the Pwnagotchi
The Pwnagotchi, a portmanteau of “pwnage” (meaning compromise or defeat) and “tamagotchi” (the virtual pet), is essentially a self-contained Raspberry Pi-based device designed for Wi-Fi auditing. Created by Italian security researcher Simone Margaritelli, also known as evilsocket, the Pwnagotchi leverages artificial intelligence to optimize its Wi-Fi hacking capabilities.
Key Features
- Artificial Intelligence: The Pwnagotchi’s standout feature is its use of machine learning to adapt and optimize its attack strategies over time. Through Reinforcement Learning (RL), it learns from successful and unsuccessful attempts to better understand the target network’s behavior.
- Passive Capture: Unlike traditional hacking tools that actively send deauthentication packets to capture handshakes, the Pwnagotchi operates passively. It discreetly monitors Wi-Fi traffic, capturing handshakes without alerting the target network.
- Compact and Portable: Housed in a 3D-printed case resembling a digital pet, the Pwnagotchi is small, lightweight, and easily transportable. Its inconspicuous design allows users to carry out Wi-Fi auditing discreetly.
- Customization: Pwnagotchi is highly customizable, allowing users to modify its behavior, appearance, and configuration. The open-source nature of the project encourages the community to contribute plugins and enhancements.

How Pwnagotchi wifi hacking device Works
The Pwnagotchi device works by monitoring Wi-Fi networks for handshakes, which are cryptographic keys exchanged when a device connects to a network. These handshakes can then be cracked offline, revealing the network’s password. The device employs a two-phase process:
- Learning Phase: During this phase, the Pwnagotchi observes and learns from the target network’s behavior. It collects data on handshakes and evaluates the network’s vulnerabilities.
- Evolution Phase: Using the insights gained during the learning phase, the Pwnagotchi adapts its attack strategy to increase the chances of successfully capturing handshakes. This continuous learning cycle makes the device more effective over time.
Ethical Considerations
While the Pwnagotchi is a powerful tool for ethical hackers and security professionals, its use raises ethical considerations. It is crucial to ensure that the device is employed responsibly and legally. Unauthorized access to computer networks or any form of malicious activity is strictly prohibited.

Exploring Alternatives of Pwnagotchi or wifi hacking device
1. ESP8266 and ESP32 Devices: One notable alternative to Pwnagotchi is the use of ESP8266 and ESP32 microcontroller-based devices. These affordable and versatile platforms are equipped with WiFi capabilities, allowing users to create custom WiFi hacking tools. Enthusiasts can leverage platforms like Arduino and MicroPython to program these devices for passive WiFi monitoring, handshakes capture, and other security-related tasks. The open-source nature of the ESP8266 and ESP32 communities fosters a collaborative environment for programming research and the development of new functionalities.
2. Wi-Fi Deauther Projects: Wi-Fi Deauther projects, often based on the ESP8266, are specifically designed for deauthentication attacks. While different from Pwnagotchi’s passive approach, Wi-Fi Deauthers actively disconnect devices from a WiFi network, forcing them to reconnect and revealing handshakes in the process. Various GitHub repositories host Wi-Fi Deauther firmware that enthusiasts can flash onto ESP8266 devices. This alternative offers a hands-on programming experience, allowing users to customize and enhance the tool’s capabilities based on their requirements.
3. BetterCap: BetterCap is a comprehensive, modular, and portable MITM (Man-In-The-Middle) framework that supports WiFi hacking among other capabilities. Unlike Pwnagotchi, BetterCap operates actively by injecting packets into the network, making it a versatile tool for network reconnaissance and penetration testing. Its modular architecture allows users to extend its functionality through plugins, encouraging ongoing programming research and the development of new features.
Conclusion
The Pwnagotchi device has carved its niche in the world of Wi-Fi hacking, offering a unique combination of AI-driven learning and portability. As with any hacking tool, users must use it responsibly and within legal boundaries to avoid legal consequences. As the Pwnagotchi project continues to evolve, it remains an exciting and educational tool for those interested in the intersection of cybersecurity, artificial intelligence, and ethical hacking.
For the more knowledgeable Contant click here –>Read New





I am extremely impressed along with your writing abilities as neatly as with the layout to your weblog. Is this a paid theme or did you modify it your self? Anyway keep up the nice high quality writing, it is uncommon to peer a nice weblog like this one these days!